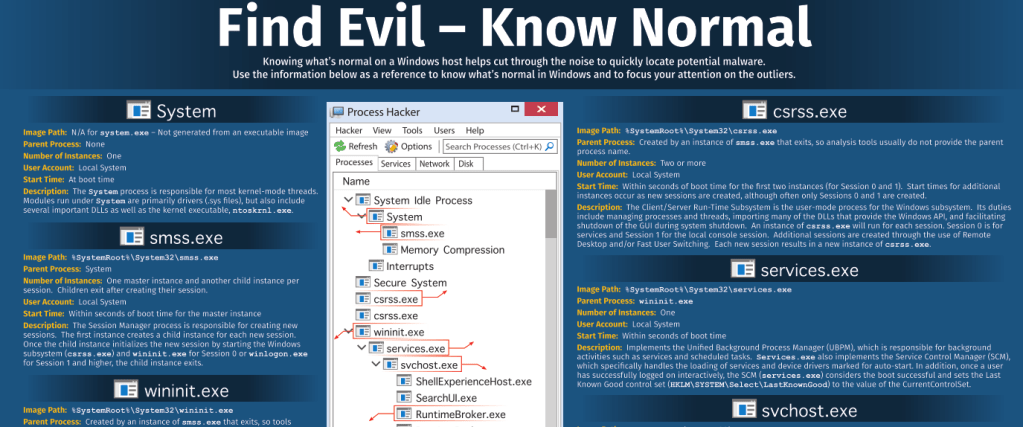
as I start getting into my labs, its pretty clear that a good understanding of the normal processes in a Windows environment is needed if you are going to know if a Windows endpoint is compromised (eg. malware executed)-although I am familiar with using ps command in linux, I am starting with Windows as its still the most common OS in use whether we like it or not.
SANS have a collection of great posters and the “Hunt Evil, Know Normal” poster is the one I have downloaded to take a look a processes like smss.exe, lsass.exe, winlogon.exe etc, and understand their parent processes, number of instances and other key details.