Category: cybersecurity
-

PCAP files
Packet Capture or PCAP files are files that contain a snapshot of network packet data. PCAPs are useful for network engineers and security analysts to see what is happening on the network, helping troubleshoot network issues by looking at TCP handshakes for example, and to defend against security threats by…
-

OT, ICT and SCADA
when we hear about financial institutions or large corporations being hacked, our first reaction may be, oh boo hoo, a company with loads of money got hacked and lost some IP or perhaps had to pay some ransom….what about when it affects utilities? ie. your heat, gas, power, hospitals, waste…
-
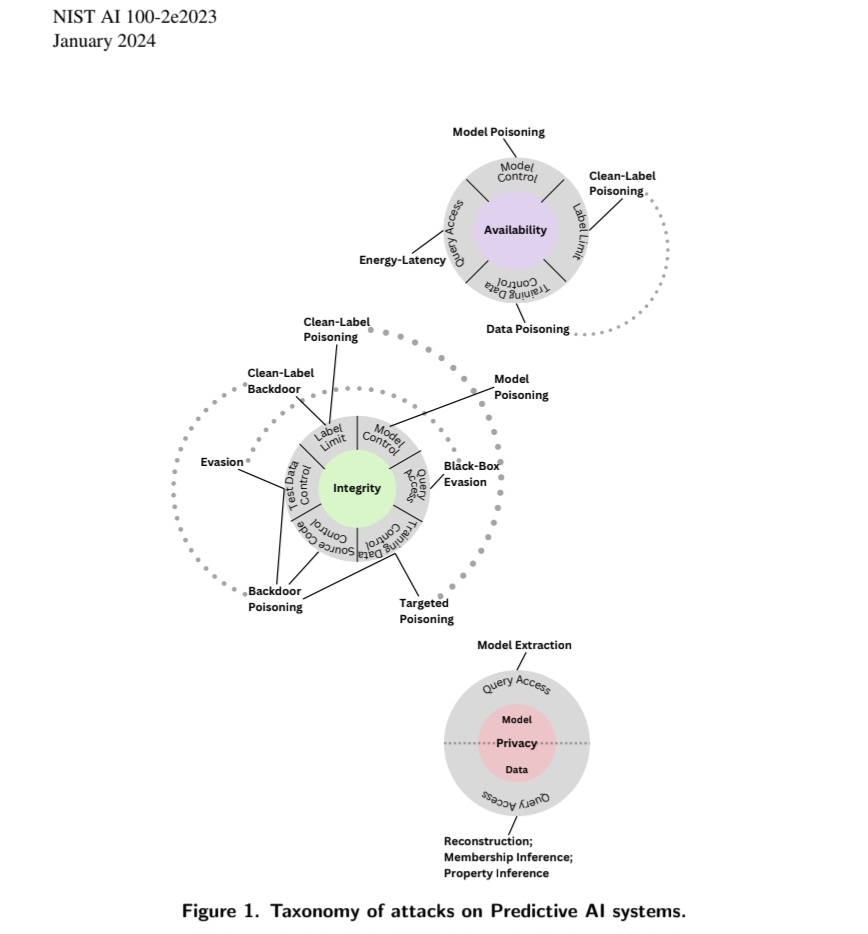
Adversarial ML – NIST document update
NIST have been publishing documents on Adversarial Machine Learning (AML) concepts and terminology, and while many have been obsoleted, the latest one is NIST AI 100-2 E2023 and can be found here: https://csrc.nist.gov/pubs/ai/100/2/e2023/final Its only about 100 pages (20 or so are reference pages) so an easy read and its…
-

PCI DSS & GDPR
PCI DSS – as many businesses utilize online payments, I wanted to take a look at the details of PCI DSS and understand it a little more – I thought it would be a fairly dry topic, but the online course I did was actually quite enjoyable and I am…
-

Mother of all Breaches
a data breach of over 26 billion records dubbed MOAB, or the “Mother of all breaches” has been discovered and currently making headlines. https://cybernews.com/security/billions-passwords-credentials-leaked-mother-of-all-breaches/ cybernews has put out a data checker to see if your data has been leaked but I’m sure SOC analysts around the world are bracing themselves…
-
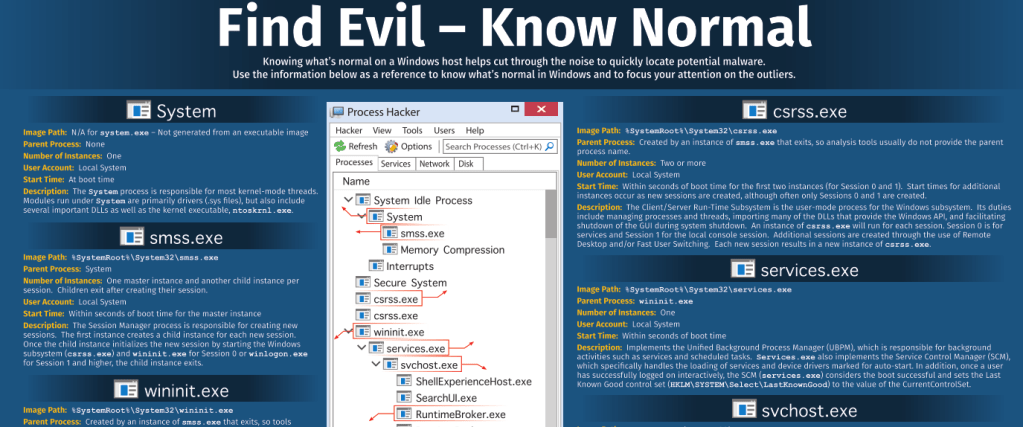
Windows Process Tree
as I start getting into my labs, its pretty clear that a good understanding of the normal processes in a Windows environment is needed if you are going to know if a Windows endpoint is compromised (eg. malware executed)-although I am familiar with using ps command in linux, I am…
-
HTB
after doing some foundational study on Coursera and other platforms, its now time to jump into some hands-on labs. I am starting with a well known “Home labs as a Service” provider, HackTheBox for now and have selected the SOC analyst learning path. My reasoning for this is that I’m…
-
AI and LLM – part 2
after my last post, it seems the algorithms did their thing and I was suggested a webinar by SentinelOne on the Impacts of AI in Security and I attended this live even though it was 3am my time as it was something I really didn’t want to miss out on…
-

What’s a CVE anyway?
reading about the recent vulnerabilities announced by Atlassian in articles such as this one, https://www.helpnetsecurity.com/2024/01/16/cve-2023-22527/ prompted me to look into what makes it become a CVE and what is the process involved, as there were assumptions I had made about legal disclosure and I was mistaken. Any security vulnerabilities that…
-

Pentest GPT
I have been using ChatGPT quite a lot these days to help with my coding studies, and there is a whole area of AI devoted to prompts so its not surprising that we are seeing Chat GPT used for automating pentesting tasks. According this article the tool was able to…
-
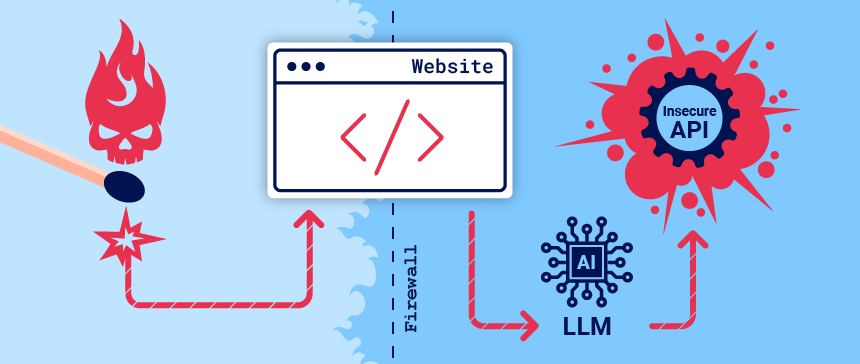
AI and LLM cyber attacks
we are starting to see a lot more articles in the cybersecurity space around the use of AI in cyber attacks. Cyber criminals like any criminal are opportunistic and will use whatever vulnerability is easy to exploit, or whatever tool that is at their disposal. This is an interesting article…
-
CISSP exam
so I have spent the last few months preparing for my CISSP exam and as I do some final revision and schedule my exam, here are a list of the resources I used and the cost involved – with the weak yen this is quite the investment… Pete Zergers’ exam…
-
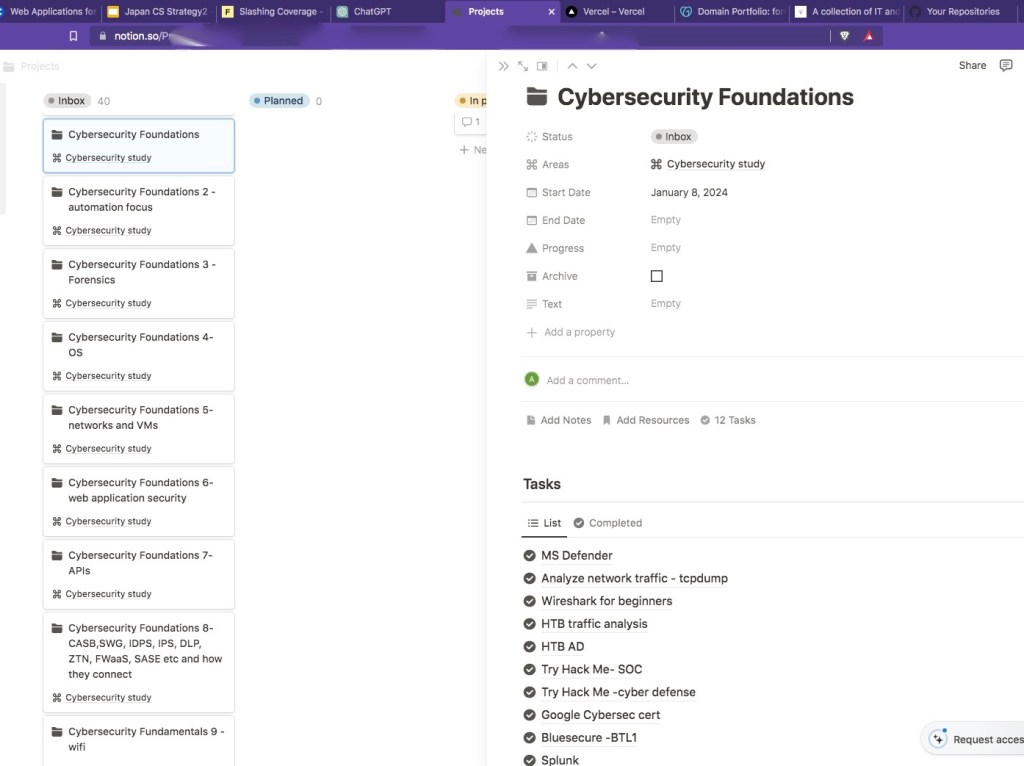
Second Brain
I had heard the concept of a “second brain” a while back and finally sat down to do some proper reading on the subject.I soon realized this would be a great way to structure my learning. I had a collection of saved URLs and text notes I wrote on my…
-
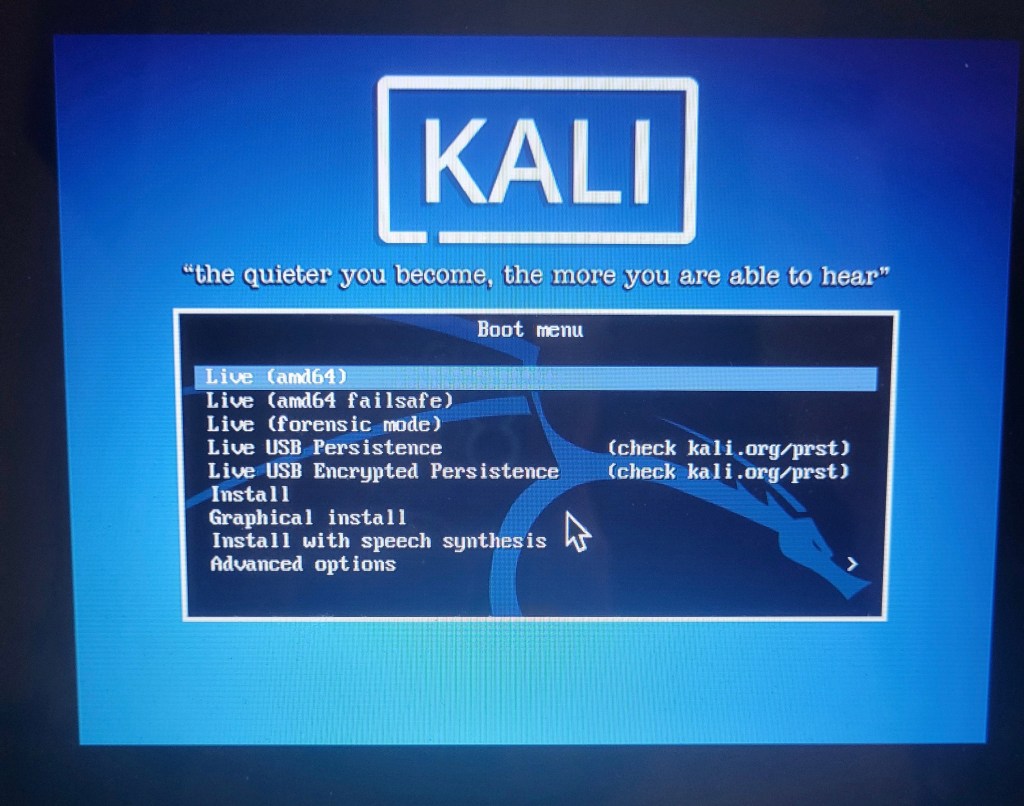
Kali linux
for pentesting and other tasks, Kali (built on debian) is the most useful piece of kit for pentesters and ethical hackers with over 600 inbuilt tools, and although I wont be jumping into using the tools just yet, I thought I had better know how to spin up a VM…